New details emerge about a data theft at National public data (NPD), a retail customer data broker that recently published social security numbers, addresses, and phone numbers of hundreds of millions of Americans online. KrebsOnSecurity has learned that another NPD data broker with access to the same retail customer data inadvertently published the passwords to its backend database in a file that was freely available on its homepage until today.

In April, a cybercriminal named US Department of Defense began selling stolen data from NPD. In July, someone leaked the stolen data, including names, addresses, phone numbers, and in some cases email addresses of more than 272 million people (including many who have since died).
NPD confirmed the breach on August 12 and said it stemmed from a security incident in December 2023. In an interview last week, the US Department of Defense blamed the July data breach on another malicious hacker who also had access to the company’s database, which has allegedly been floating around underground since December 2023.
Following last week’s story on the extent of the NPD breach, a reader alerted KrebsOnSecurity that a sister company of NPD – the background search service recordscheck.net – hosted an archive containing the site administrator’s username and password.
A review of this archive, which was available on the Records Check website until just before its release this morning (August 19), shows that it contains source code and plaintext usernames and passwords for various components of recordscheck.net, which visually resembles nationalpublicdata.com and has identical login pages.
The uncovered archive named “Members.zip“” indicates that all RecordsCheck users were initially assigned the same six-digit password and asked to change it, but many did not do so.
According to data leak tracking service Constella Intelligence, the passwords contained in the source code archive are identical to the credentials disclosed in previous data leaks involving email accounts belonging to the NPD founder, an actor and retired Florida sheriff’s deputy named Salvatore “Sal” Verini.
By email, Mr. Verini said that the exposed archive (a ZIP file) containing recordscheck.net’s credentials had been removed from the company’s website and that the site would cease operations “in the next week or so.”
“As for the zip file, it was removed, but it was an old version of the site with non-working code and passwords,” Verini told KrebsOnSecurity. “As for your question, this is an active investigation that we cannot comment on at this time. But as soon as we can, we will be with you as we follow your blog. Very informative.”
The leaked source code of recordscheck.net indicates that the website is operated by a web development company based in Lahore, Pakistan, called www.creationnext.comwhich did not respond to requests for comment. On the CreationNext.com homepage there is a positive recommendation from Sal Verini.

A review by Sal Verini on the homepage of CreationNext, the Lahore (Pakistan)-based web development company that apparently developed NPD and RecordsCheck.
There are now several websites dedicated to helping people find out if their social security number and other data was exposed in this data breach. One of them is npdbreach.com, a search site run by Atlas Data Privacy Corp. Another lookup service is available at npd.pentester.com. Both sites show that the NPD had old and largely inaccurate data on Yours Truly.
The best advice for those concerned about this breach is to have their credit file frozen with the major consumer reporting agencies. Freezing your file makes it much harder for identity thieves to open new accounts in your name and limits who can see your credit information.
Blocking is a good idea because all the information identity thieves need to assume your identity is now widely available from numerous sources due to the large number of data thefts we have seen involving SSN data and other important static personal data.
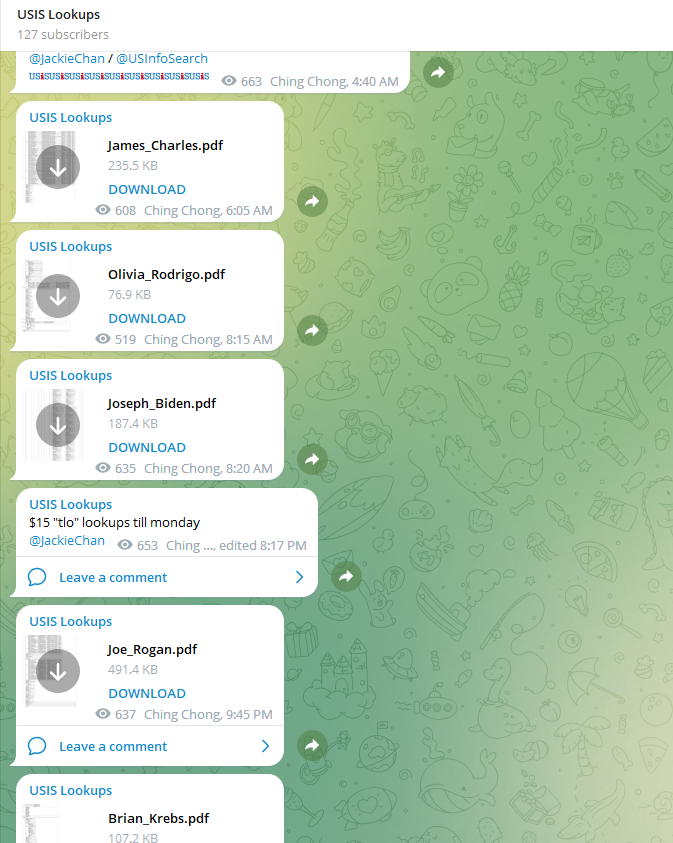
Screenshots of a Telegram-based identity theft service that sold background reports through hacked law enforcement accounts on USInfoSearch.
There are numerous cybercriminal services that offer detailed background checks on consumers, including full Social Security numbers. These services are operated from compromised accounts at data brokers that serve private investigators and law enforcement officials, and some are now run entirely automated via Telegram instant messaging bots.
In November 2023, KrebsOnSecurity wrote about one such service being run by hacked accounts at US consumer data broker USInfoSearch.com. This is notable because the leaked source code indicates that Records Check created background reports on individuals by querying the NPD database and records at USInfoSearch. KrebsOnSecurity has reached out to USInfoSearch for comment and will update this story if they respond.
The point is: If you’re an American who hasn’t frozen your credit files and hasn’t yet fallen victim to new account fraud, chances are identity thieves just haven’t gotten around to finding you yet.
All Americans are also entitled to receive a free copy of their credit report from each of the three major credit bureaus every week. Previously, consumers were allowed to receive one free report from each of the credit bureaus annually, but in October 2023 Federal Trade Commission announced that the credit bureaus have permanently extended a program that allows you to get a free check of your credit report once a week.
If you haven’t done so in a while, now would be a good time to get your files in order. To initiate a freeze, you’ll need to set up an account with each of the three major credit bureaus, Equifax, Experian and TransUnion. Once you set up an account, you should be able to view and freeze your credit file. If you find errors, such as random addresses and phone numbers you don’t recognize, don’t ignore them. Dispute any inaccuracies you find.
